This week on Mobile Security Misconfigurations
-
Although tools such as MobSF may flag it as this as a mis-configuration, it can be exploited even with a device that does not have root per mission. This mis-config can be used to create a full backup copy of the whole device including the application data that is supposed to only be accessed by root user.

For this i was able to demonstrate a PoC for the issue using bash script that i wrote to try and exploit the mis-configuration.
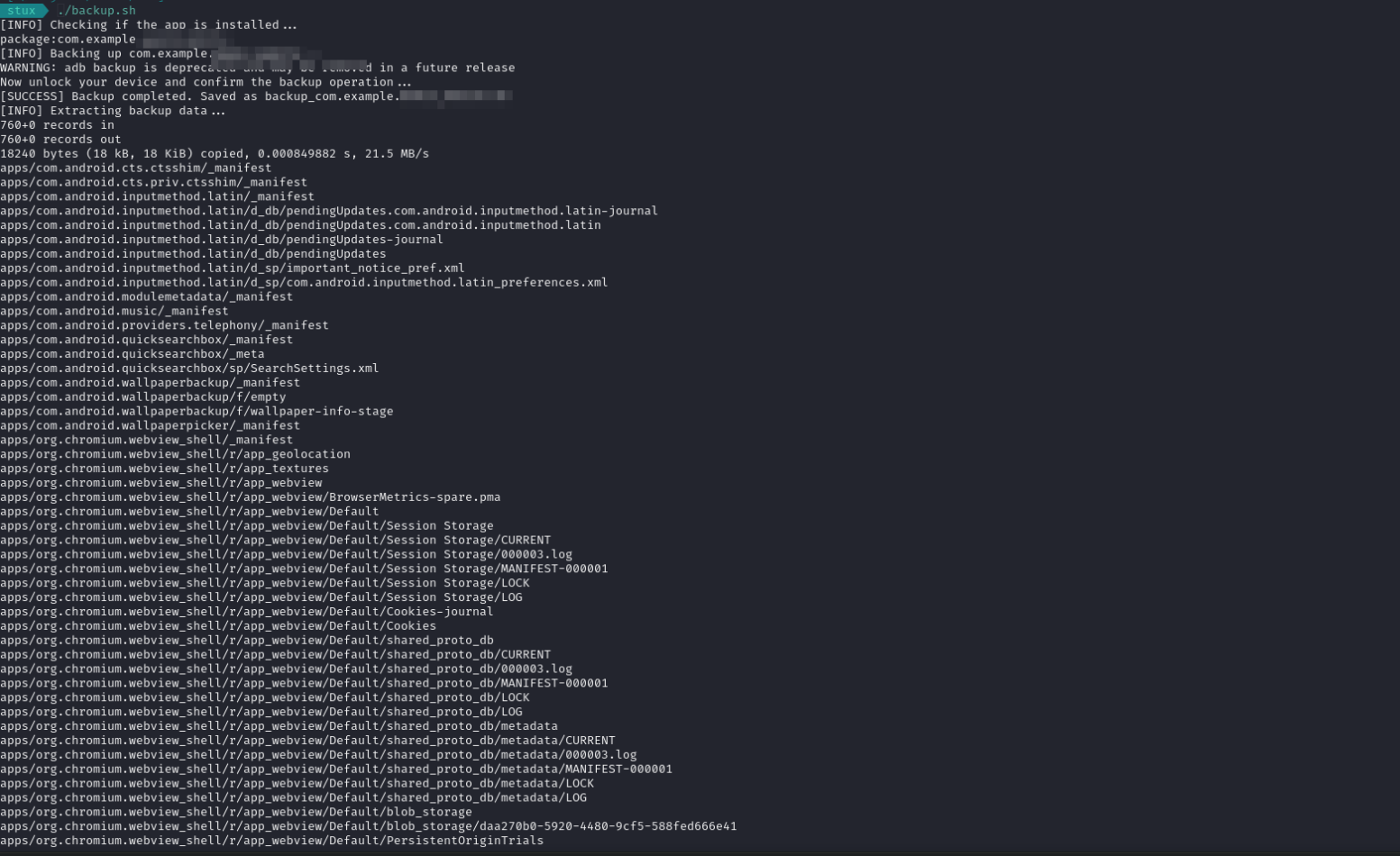
This illustrates how one application with such a misconfiguration could result to the compromise of the whole device
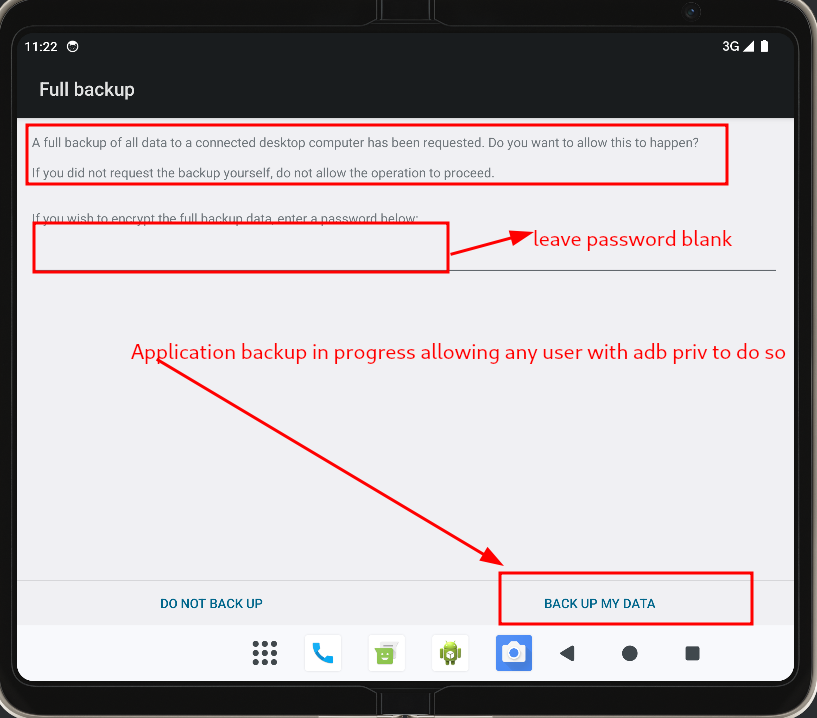
By allowing this action this means all application data can be backup.
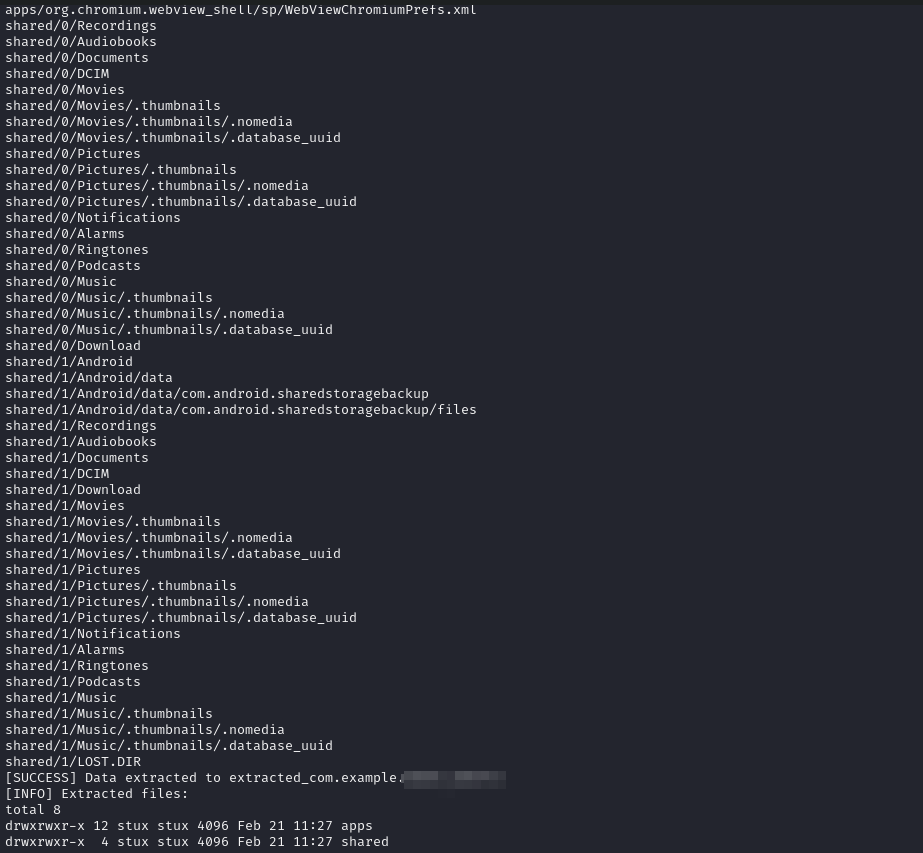
Example of data that can be pulled
what are some of the steps that can be taken in this particular case. Its quite simple
The flag [android:allowBackup] should be set to falseHappy Hacking